Your all-access pass to Cybersecurity: Combating Modern Threats with Graph Databases
-
22:10
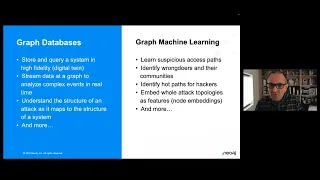
Cyber Threats and Resiliency Landscape
-
41:27
Digital Twinning the Cloud for DevSecOps
-
16:40
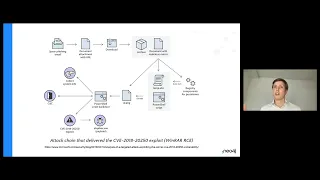
The Role of Graphs in Cybersecurity
-
22:06

The CI/CD Graph – An Attacker’s Perspective
-
33:38
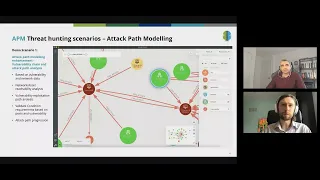
Graph-based Threat Modeling, Security Analytics, and Threat Hunting
-
23:51
From Cyber Events to Cyber Stories
-
30:01

Modeling Cybersecurity with Neo4j, Based on Real-Life Data Insights